One of a network team’s most important responsibilities is ensuring configuration consistency. To maintain standards and configuration compliance, teams must implement, secure, and enforce configurations across their ENTIRE hybrid cloud network.
Configuration management has become more complex in recent years as network environments evolve. Cloud migration, moving resources to the edge, multiple clouds, evolving cybersecurity threats and more have created a landscape where teams must manage a high volume of policies and configurations across multiple domains – data center, cloud, SD-WAN, etc. If something is configured incorrectly, it can be scary and keep you up at night, especially if it’s a Friday (the 13th).
With this challenging configuration management landscape, over time, unexpected things can occur — whether down to mistakes, technology changes, personnel turnover, anything. Things that can only be seen when they want to be seen… things that tend to hide in the dark… and things that can haunt your network infrastructure unknowingly… ghost configuration, BOO!
Ghost configuration is one of the spookiest aspects of managing a network. It can hide in plain sight, it can cause trouble without you knowing, and most importantly — it can haunt your network, anywhere in your infrastructure.
Most network teams don’t even think about ghost config until they’ve encountered a full torso apparition and need to call in the Ghostbusters. But it’s too late. By then, the ghosts in your configuration have manifested themselves into a full-blown network haunting. So the question is, how do you hunt down the ghosts in your network configuration BEFORE they spook you?
What Makes Ghost Configuration So Spooky for Network Teams
The term ghost configuration sounds spooky by nature, which is pretty accurate. But what does it actually mean? Let’s level set and define it so you understand how to find it.
Network teams are responsible for implementing standardized configurations across their network. This is done to ensure that the network is optimized, addresses the exact needs of the organization, and is secure.
However, most network teams struggle to keep up with the complexity of their environments using existing configuration management tooling. Sometimes, for testing, troubleshooting, or other time-bound reasons, teams can end up adding rogue configuration that can often go unnoticed or forgotten. Some piece of config, on some device in some domain, that’s been there a while, but nobody knows what exactly it does, only that they’re not going to risk deleting it. The rogue configuration ends up staying on the device, inevitably creating a ghost config that is only found when it’s actively hunted down.
There are typically four types of ghost configuration you can encounter on a haunted network:
Ghost 1: Slimer, Pure Havoc
Nefarious configuration left by someone who shouldn’t be on your network. Someone could be purposely leaving bad configuration on your network such as creating a pinhole to allow bad traffic in. You can equate this to Slimer, purposely causing havoc everywhere here goes.
Ghost 2: Stay Puft Marshmallow, Cute yet Detrimental
Inadvertently forgotten configuration that was added for testing or troubleshooting purposes. While this seems harmless at first, it could actually end up being detrimental. A prime example is a rogue filter or access list configuration that was left on a device that could allow the wrong traffic through or block the right traffic from coming in. You can equate this to the Stay Puft Marshmallow Man, cute on the outside but full of terror on the inside.
Ghost 3: Casper, the Friendly Ghost
Busy network teams not correcting configurations, thinking they are harmless. Someone often notices that certain “harmless” configurations are not correct, but it takes too long to determine what the right information is, and there are more pressing things happening on the network. You can equate this to Casper, a seemingly friendly ghost, but a ghost nonetheless that can grow and cause problems later.
Ghost 4: Librarian Apparition, Harmless but Annoying
Network teams do like to have fun sometimes (but shhhh keep it down), leaving little messages, easter eggs of sorts, in the configurations. While these additions might be harmless, such as adding a description that contains a message, the addition while not affecting the network, falls outside of the organization’s standards.
While the position of many network engineers is to do no harm, ghost configs if left alone can over time cause harmful and unintended consequences that can bring risk to your network — shutting down good traffic, letting in bad traffic, setting your time server off, and much more. (Queue the sPoOoOkY “IT and Security Auditors” soundbite.)
Ghostbusters: Validating Your Config
Now comes the fun part – how do we bust these unwelcomed ghosts in our networks?
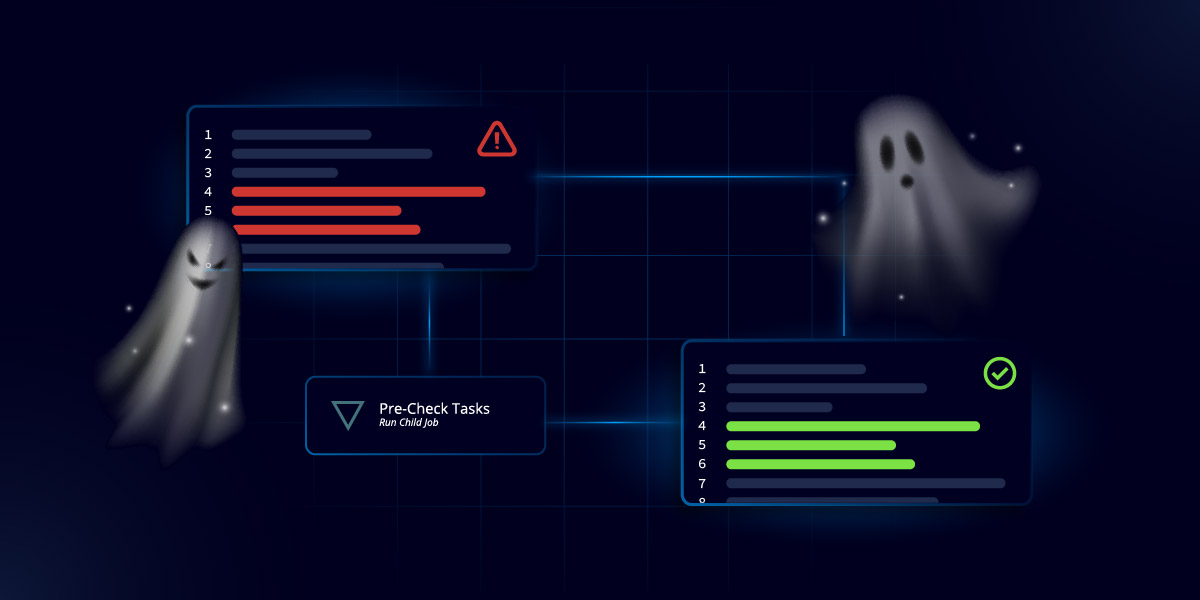
The first step is to determine if it’s even a real ghost or not. It may not be part of your Golden Configuration, but it could still be a necessary piece of configuration that someone added without documentation on why. When you find something that seems a little ghostly, you must first investigate and validate if that config is a real ghost or real config.
Whether it’s a policy change, routing change or something different, you must ensure that by busting that ghost configuration you don’t cause any unexpected effects, reversing the intended effect of this change. If you remediate that change without validating whether it’s needed first, you might end up breaking things in a way you didn’t predict (which is why ghost config is so common in the first place).
Who You Gonna Call? Itential!
Just like most scary things, human nature is to avoid ghost config. Especially if you don’t have the right weapons to help you overcome that scary thing.
It is inevitable that ghost configuration haunts every network (yes, even yours). At Itential, we have the tools you need to bravely take on those spooky spirits hiding in your network. Think of us as your proton pack, finding and trapping your ghosts so you can successfully contain and eliminate them.
Our network configuration management capabilities make it easy to set up automation to detect and alert you if any ghosts appear in your configurations so you can determine if they’re real ghosts or real config. If something turns out to be a spooky ghost, you can then set up automations to quickly identify and remediate the auditor writeups and ghosts.
Ghosts can pop up anywhere across your network, which is why Itential’s configuration management capabilities are built for today’s hybrid environments.
Itential’s advanced capabilities to meticulously manage configuration, compliance, and reporting for a wide array of network devices and cloud services enable infrastructure teams to uphold the highest standards of security and performance for business-critical applications ¬– across cloud, data centers, and security domains. Teams use our platform to eliminate misconfigurations across their networks, achieve compliance for multi-vendor infrastructure, and orchestrate real-time changes.
By using Itential for multi-vendor, multi-domain configuration management and validation, teams can easily detect ghost config across the network and remediate anything that’s out of standard.
The next time you see a ghost in your network, who you gonna call? Itential!
To learn more about our network management capabilities, feel free to browse these configuration management demos.