Share this

I’m always amazed at how much information about networking is rattling around in a network engineer’s brain. The more time they spend in the trenches of networking and around specific network environments, the more information they pick up and store away as tribal knowledge in their own heads. They are able to recall things like CLI commands, IP addresses, DNS information, routing configuration, and much more almost immediately. If I were to ask a network engineer to configure a router “from scratch,” how much could they configure only from the information in their head? In some cases, they may be able to configure the device in a way that it can immediately be put into service, but does that mean the configuration is complete? Does the configuration represent the most secure, most reliable, and highest performing configuration possible for that device?
What is Golden Configuration?
They wouldn’t really know it was “complete” in this sense unless there was a pre-existing, pre-defined standard to compare this configuration to – this is Golden Configuration. Organizations that lack the ability to create this standard, and a process to apply this standard, may find that every device in the network is missing some areas of critical configuration that make it less secure, less reliable, or less efficient. And this is a scary proposition, because organizations rely on their networks more than ever and the growth of cloud networking has exposed more of the network to the public. This results in a greater need than ever to ensure that every network device and service is configured correctly and adheres to the same standards set by a Golden Configuration.
In today’s modern world of network complexity, the network team needs a reliable method of defining Golden Configuration standards that can be applied to network elements that are managed by either CLI or API. With API being a more modern method of management, many traditional tools do not provide support for APIs or require external programs and custom code, which requires a programming skillset and the time to make it work. Most network teams don’t have the background or the time to go that route, so a new approach to building Golden Configurations is necessary to enable network teams to build robust and secure networks, whether on-premises or in any cloud platform.
How to Apply Golden Configuration with Itential
Itential provides a much-needed modern solution so network teams are able to quickly build a Golden Configuration for a group of devices by leveraging existing CLI or API configurations. Then, they can organize them to determine which sections are more static and globally applicable to multiple devices and define other sections of configuration which are more relevant to smaller sets of devices. This creates a natural hierarchy, or tree structure, of configuration sections where more globally relevant configuration is organized at the base layers, and at the end branches, configurations can get more specific. This provides the ability to create a single Golden Configuration tree that is relevant for potentially dozens or hundreds of devices, instead of having dozens or hundreds of unique “Golden Configurations” for every single device. By leveraging Itential, network teams are allowed the dynamic definition of areas of configuration by the use of variables and Jinja2 templates as well as the ability to define rules and severity for each line of configuration. Once all of this is defined in the application, network engineers have a standard configuration to check across new and existing devices to ensure they are complete and in compliance, and never have to second guess because they are forced to rely on memory alone.
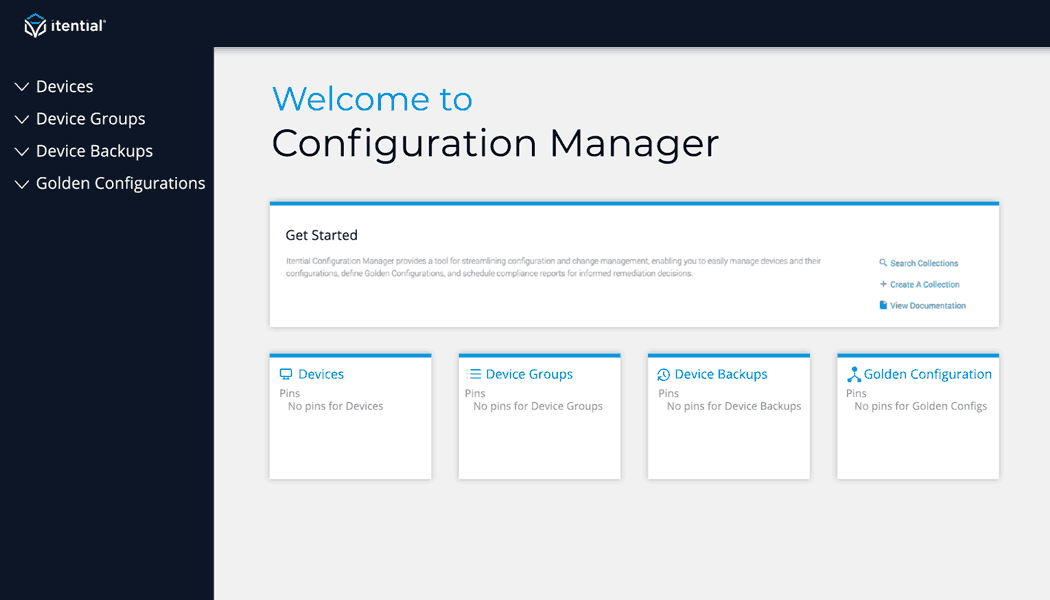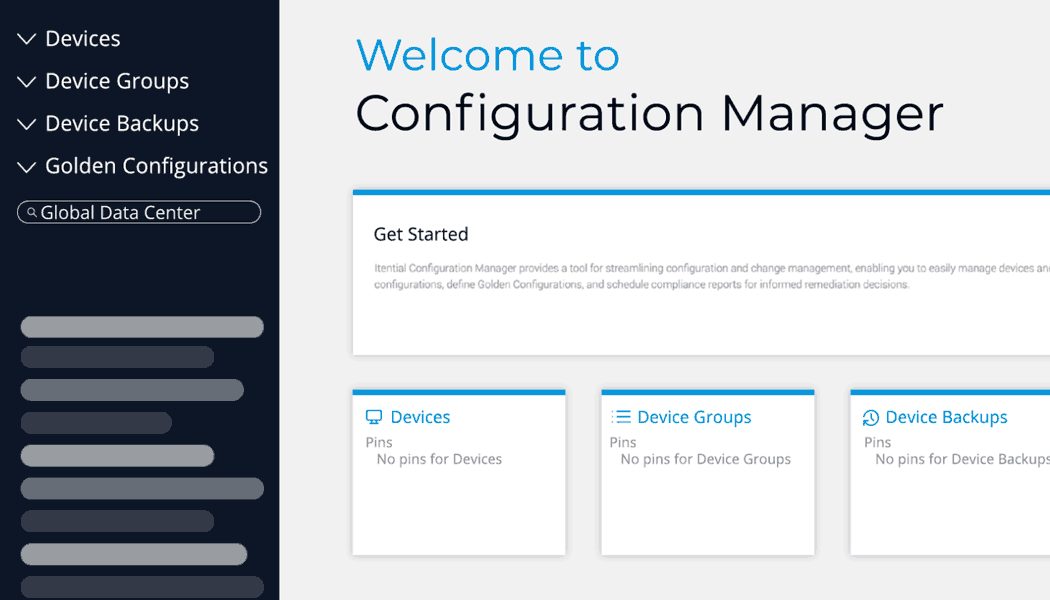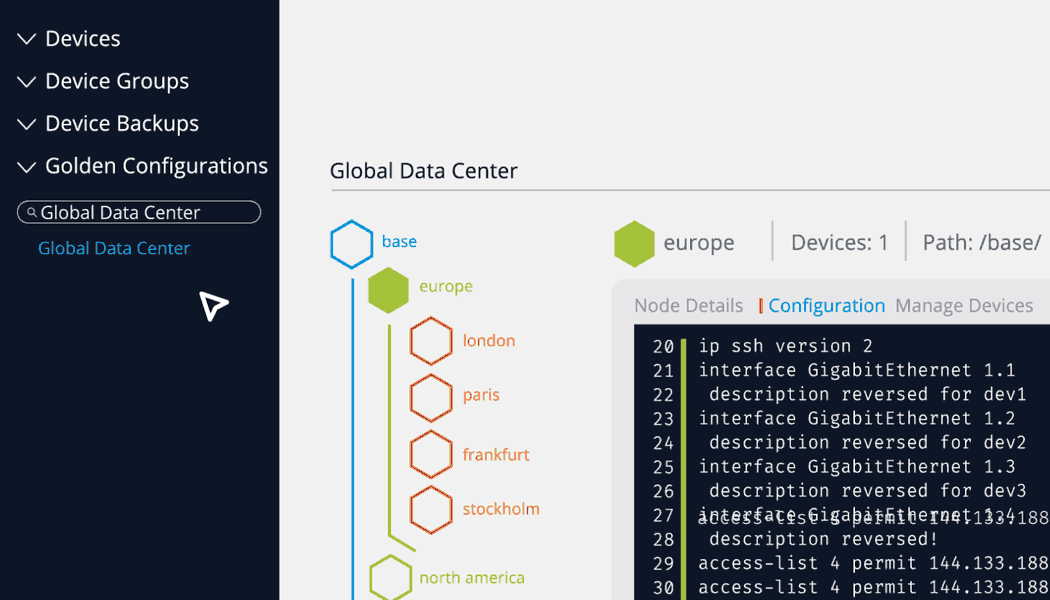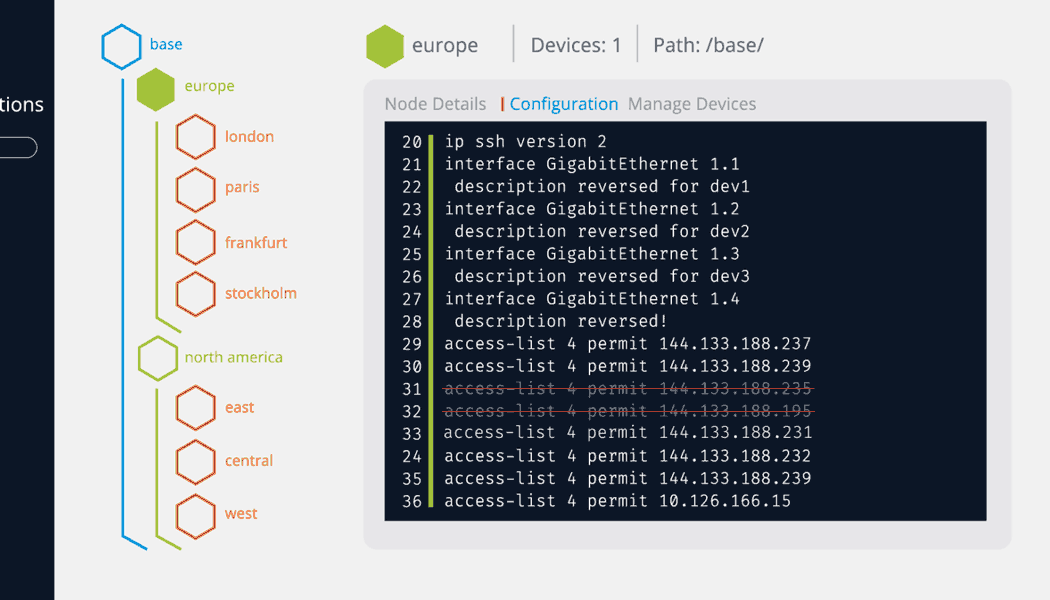
With Itential’s Configuration Manager, network teams have a modern solution for every step of their automation journey. Using the federated inventory, which includes both CLI-based traditional network devices and API-based network solutions and cloud services, teams can select any network component and create a backup configuration, view the current configuration, or compare any previous backup configuration to the running configuration and immediately see the differences without having to manually ‘stare and compare.’ In addition, Itential’s platform enables network teams to build configuration standards, run compliance checks across the entire network, and remediate any device’s configuration to bring it back into compliance. To learn more about Itential’s approach to modern configuration and compliance click here or check out and register for our webinar series on “Modern Network Compliance.”





