Network to Code, a network automation solutions provider, recently released the findings of their annual NetDevOps survey, which aims to better understand how network operators and engineers are using automation to operate their networks. This recent survey showed not only a continuation of the network automation movement but, how organizations are still on a constant slow and steady pace toward being fully automated, with only 66% of the respondents in the works of beginning to implement some sort of automation in a significant way for the past two years or less.
Low Hanging Fruit of Network Automation
Part of this slow and steady pace shows that most organizations are still going after the low hanging fruit of network automation. Initial “Day 0” deployments are a popular use case, which makes a lot of sense as many deployments like this are highly repeatable procedures with little to no blast radius if there are any problems. In addition to this, certain technologies like SD-WAN, come with a set of tools and controllers that make it a lot easier to automate deployment within that domain. It’s also a very good idea to start off with a solid baseline configuration (a Golden Configuration) that may include management and security policies that must be consistent across the enterprise, and automating initial deployments ensures that every configuration is normalized to these policies.
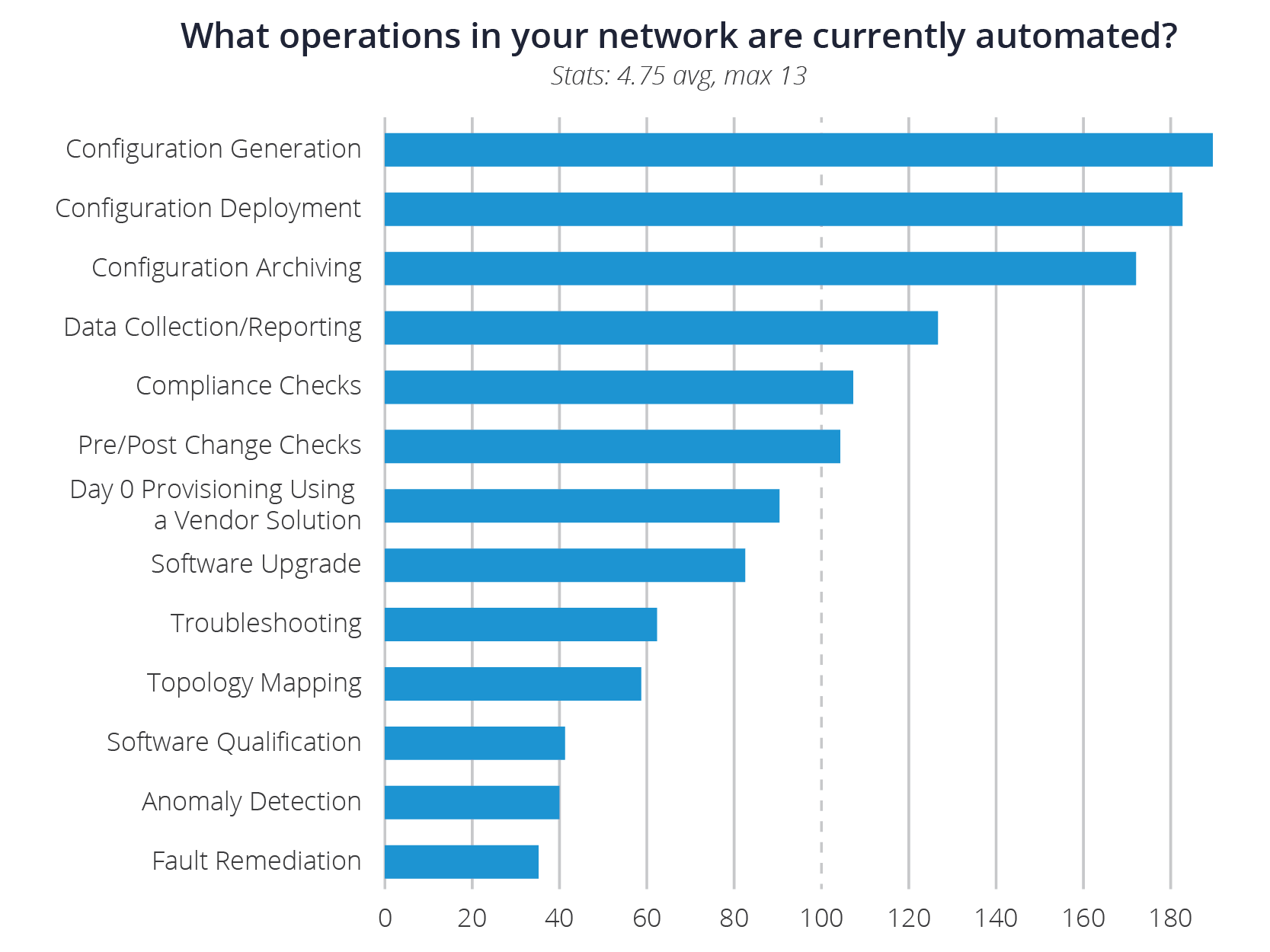
Another popular set of tasks to automate noted by the survey results are the processes around archiving and versioning configurations on different network devices. This also makes a lot of sense since quickly recovering from a hardware failure would require having the latest configuration available, and this is a task that doesn’t get a lot of attention until there actually is a hardware failure, which could be too late. This is a very common task with a lot of existing tools to that are easy to use and deploy. Again, the blast radius for this task is quite small, and the insurance it provides is considerable if there’s any kind of hardware problem or configuration drift.
With a database of current configurations that are available due to automating configuration backup tasks, the next logical step would be to check those configurations for compliance based on defined security policies. From a security perspective, this is very top of mind and when the mandate gets to the networking team, it becomes a real challenge. Organizations in the survey averaged between 250 to 5000 network devices, and these devices may come from multiple vendors with different CLI interfaces. All of these devices need to reflect the most up to date security policy, and that’s a staggering amount of checking for a human to manually check. Additionally, any device that fails to meet the configuration standard will ultimately be remediated and updated, so there’s additional process for the networking team after finding devices that are out of compliance. This can create a tremendous backlog for teams, and can quickly grow so large that it may take weeks or months to accomplish. Automation for checking configuration drift will be important, but the next step is to allow automated remediation of the devices that are out of compliance.
The Need for Network Automation
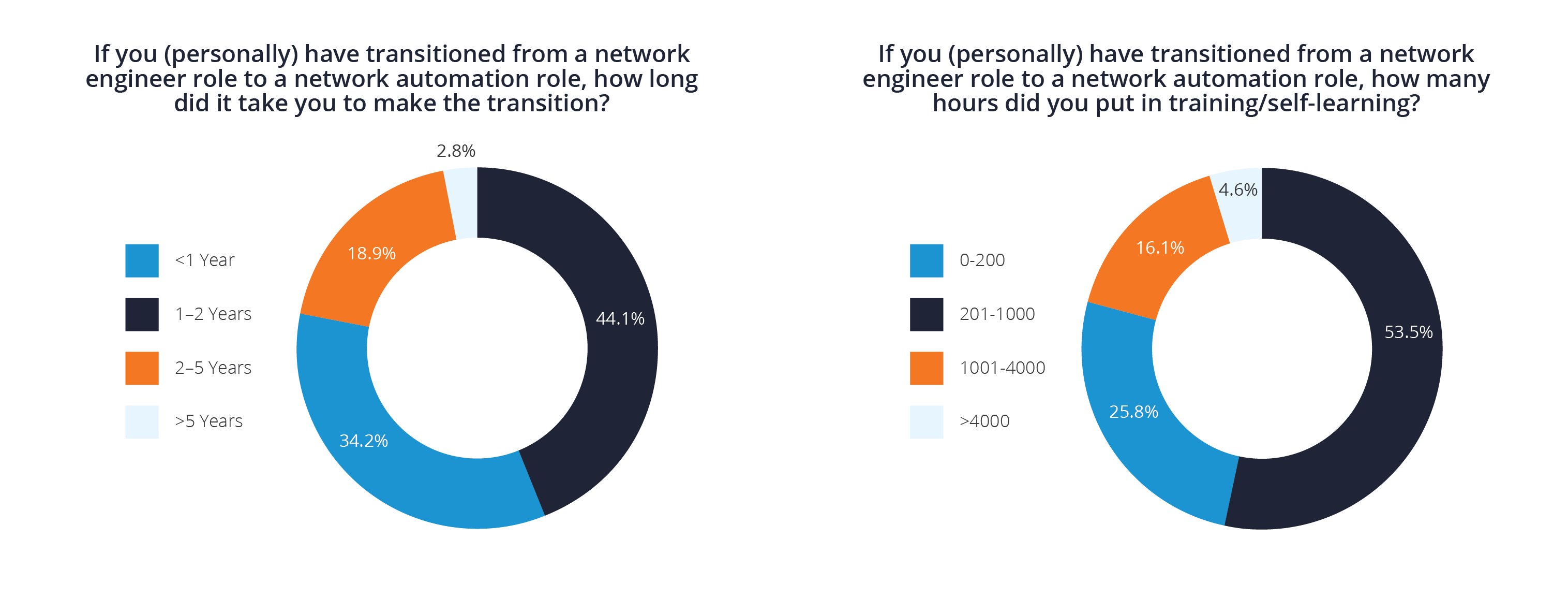
Getting started into Netops/DevOps is a challenge that is going to require a considerable amount of time and discipline. Based on the survey results, the primary tools for network automation revolve around Ansible, GIT and Python. Along with these tools, expect to also learn the Linux operating system and its various services, Python, package management, YAML, shell scripting and much more. Participants in the survey estimate that they have invested between 200 to 1000 hours for the transition into the NetOps/DevOps world, depending on previous skill sets and this investment of time will primarily occur outside of work. Networking demands are increasing, therefore the amount of tools needed to manage networks is increasing, and the backlog of network tasks is increasing. More and more network changes need to be completed with the same staff and in the same maintenance window schedule, causing more work than can actually be accomplished. In addition to this, expect to spend 6 months to 2 years to make the transition with these tools, with very little structured training. It will take a disciplined mind that is willing to work a full day and sacrifice their personal time to make this journey. Unfortunately, enterprises don’t seem to have a real focus on empowering their networking teams into automation, but it is clear that automation is needed immediately.
Overcome the Skills Challenge with Itential
As the survey shows, there are many tools, many systems, and more complex networking technologies along with constant day to day changes to the network that NetOps teams are constantly challenged with. Organizations don’t have the time or resources to allow on-the-job training, and it will require a personal sacrifice in time to learn these new skills for new tools, and that will require months and months of disciplined learning to accomplish. Automation of networking tasks and automation across multiple domains is an immediate need and organizations don’t have the luxury of taking time to train up on these new skills. At Itential, we have created a network automation platform that can provide immediate value to the networking and IT team by allowing teams the ability to easily build their own automations in a drag and drop, low-code environment, by integrating with the tools and systems they already use. By leveraging the Itential Automation Platform, teams don’t have to spend 200 to 1000 hours to transition the NetOps/DevOps world, they’ll be immediately plugged into it.
These insights are just the tip of the iceberg. Stay tuned for more findings from the Network to Code NetDevOps survey in our next blog post.


