Traditional methods of configuration validation rely on detecting a bad configuration after it has already been applied to a device. By instituting a validation process, enterprises can avoid the break-check-fix cycle of configuration compliance and validate whether a proposed configuration change is compliant before it is applied to a network device.
Network Configuration Management Automating Network Configuration Validation
Is the Lack of a Modern Configuration Validation Process Holding You Back?
Legacy network configuration compliance management solutions take a break-check-fix approach to ensuring network compliance.
- First, someone makes a change to a network device that violates a rule, thus breaking the defined standard.
- Next, a process is run which checks the network device for configuration changes and identifies the change and determines that the device is now out of compliance.
- Finally, the device’s configuration needs to be rolled back, modified, or deleted to bring it back into compliance which “fixes” it once again.
Relying on this methodology alone in today’s security-driven environment results in greater exposure to security risks and potential network outages. To understand how much time this exposure may last, simply determine the amount of time it takes before a bad configuration change is made and properly remediated—or to put it another way, the time between break and fix.
Instead of relying solely on the break-check-fix methodology of legacy solutions, modern solutions should also implement a process of configuration change validation. Validation makes configuration compliance checking into a proactive process instead of a reactive one.
Before a change is applied to a network device, it must first be validated by an application. The application will take the proposed configuration changes, and answers the following question: “If these configuration changes are applied to this network devices, will it violate the currently defined compliance standard?”
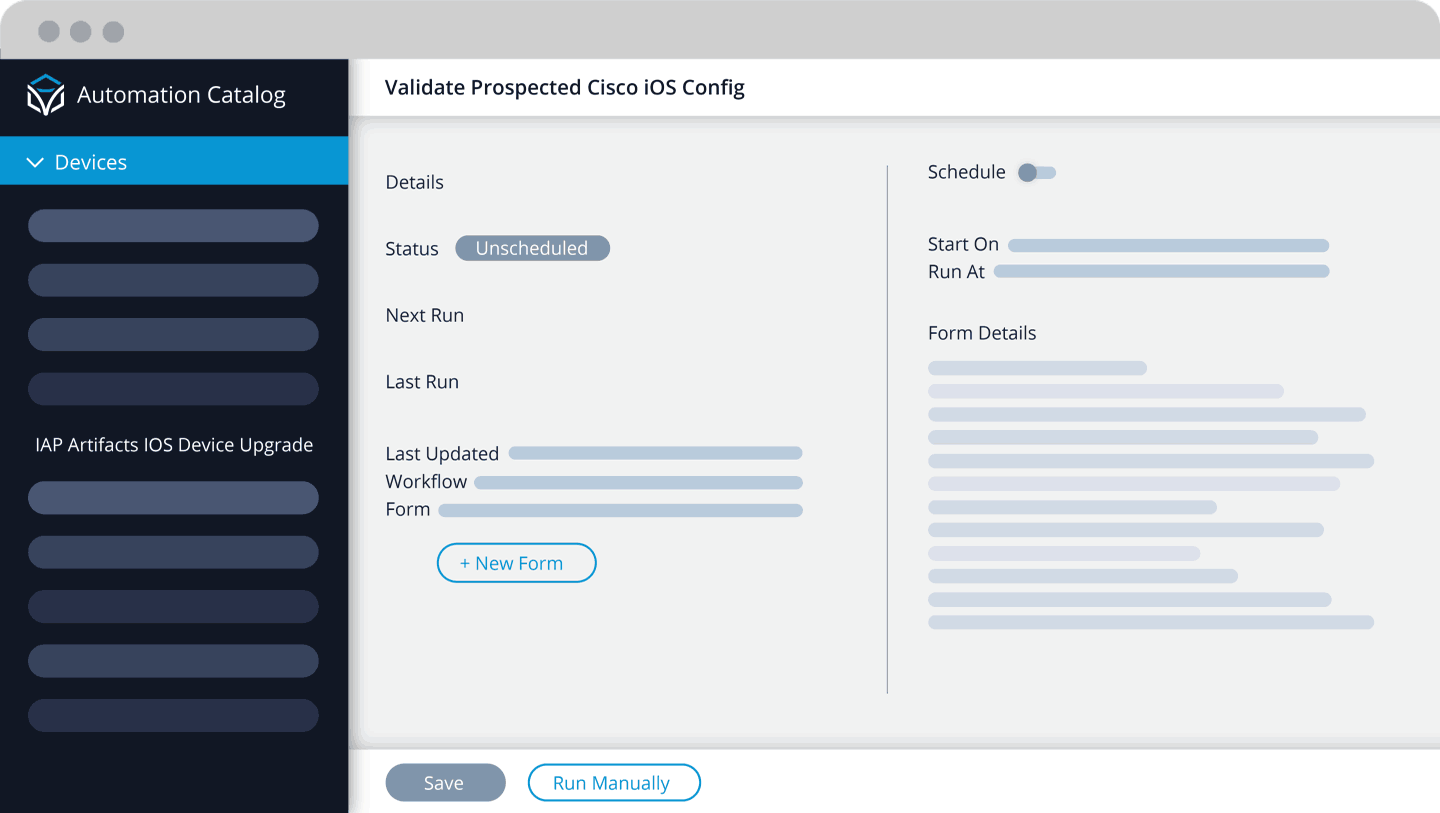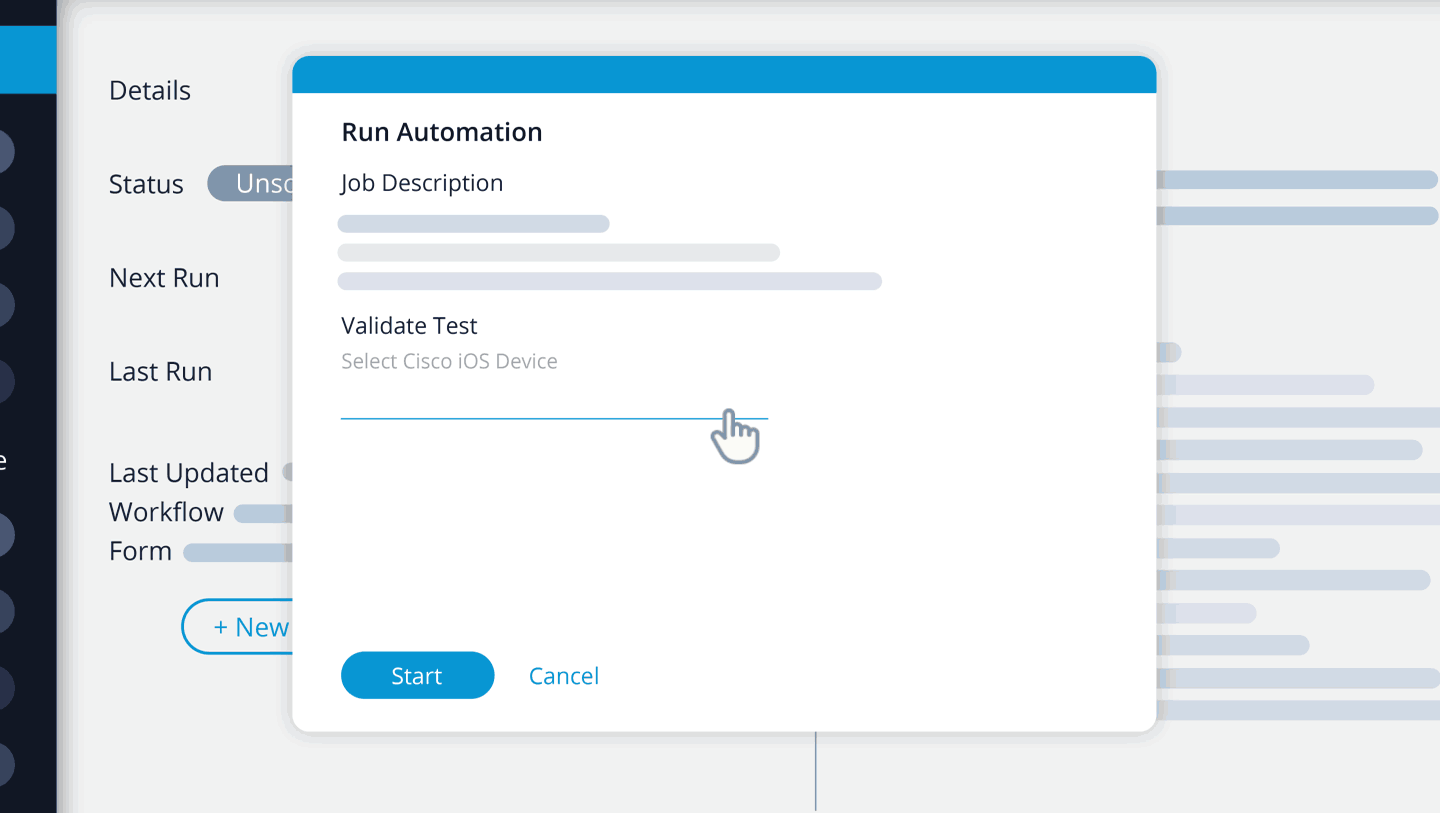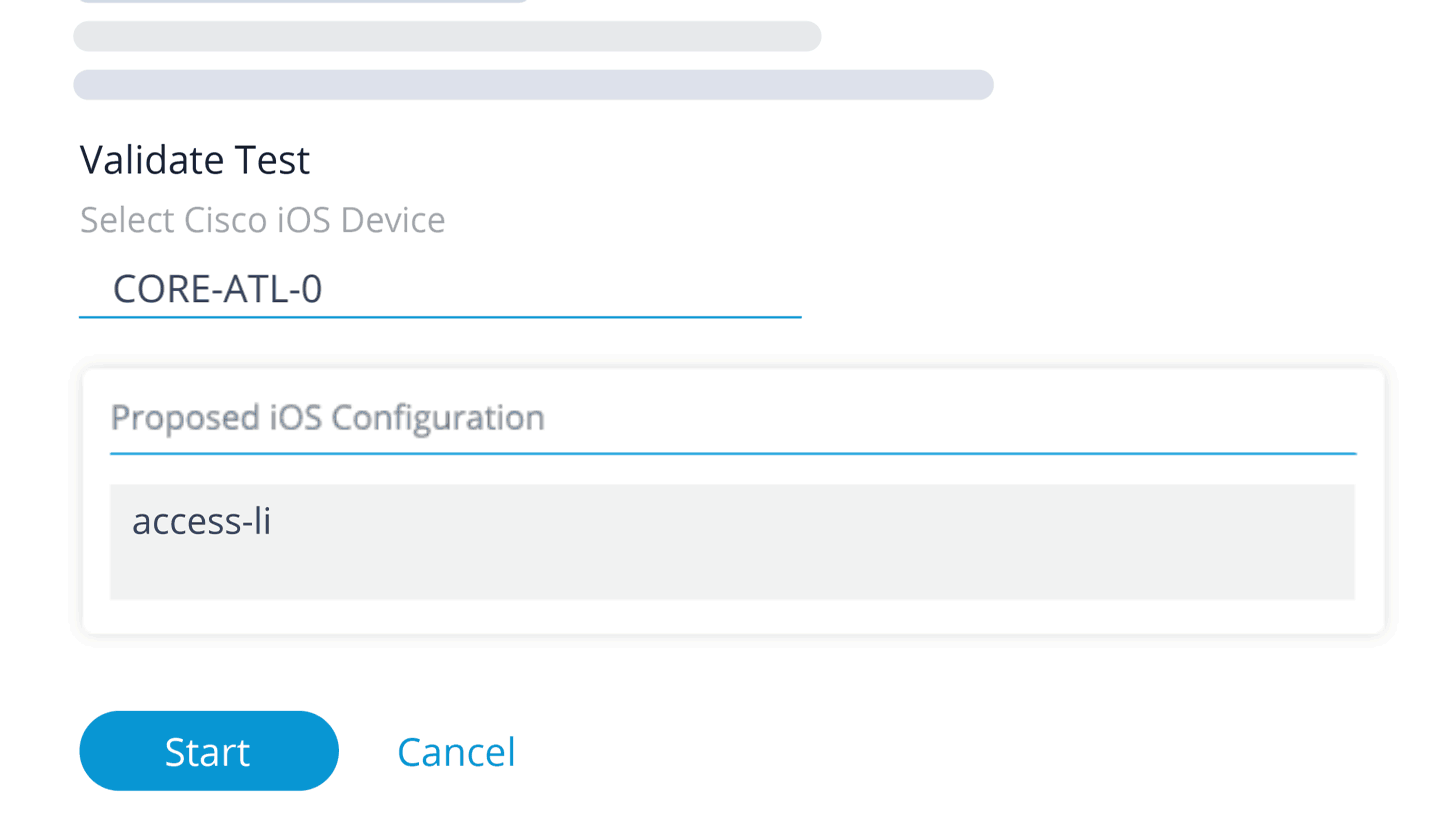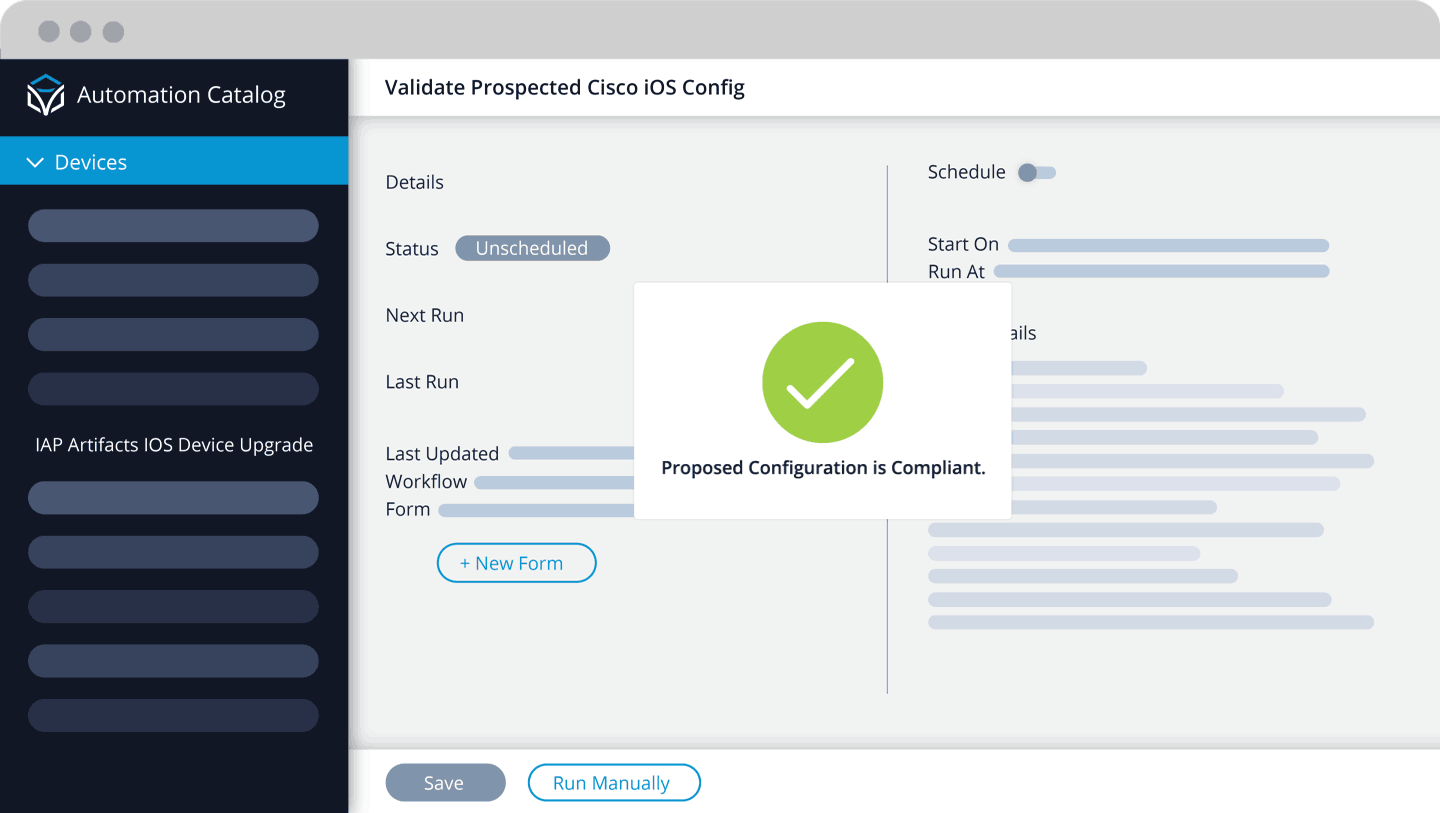
- If the response is “No,” then the configuration changes will not break the compliance rules and they can be applied to the device.
- If the response is “Yes,” then the proposed changes will break compliance, and they should not be applied.
By implementing a validation process into the process, enterprises can always be sure that the network stays in constant compliance.
So ask yourself, are you still:
Only using traditional, reactive network configuration compliance checks?
Many enterprises still rely on manual methods of compliance checks on a limited number of network devices. If you’ve implemented an automated method of network compliance checking, that’s a good start but it still leaves a window of opportunity for devices to become unnecessary risks due to configuration changes that cause out of compliance.
Concerned at the number of network changes that occur across the network?
Any configuration change to a network device has the potential to take it out of compliance. If there are many changes occurring across many network devices, there’s a good possibility that one or more of these devices are out of compliance and depending on the nature of the change, the device may be a severe risk to the network and to the overall business.
If yes to either of these, it’s undoubtedly time to automate.
Every enterprise network is critical to the overall health and operations of the business, and network teams work hard to ensure that the network is operating securely and reliably. However, there’s a limit to what a team of the most talented network engineers can do manually, and they need modern tools to help them use automation to get their networks into a state of compliance, and then make sure it stays in a state of compliance, even with a lot of network changes occurring every day.
Enterprises must have a robust, automated process that can ensure that every network device and service is operating based on a current configuration that is within the compliance standard. Automating this process is required due to the number of devices in the network and the amount of time it takes to manually perform this process. By automating reactive compliance checking along with implementing proactive validation checking, the network will operate more securely and reliably.
Why It’s Time to Modernize Your Current Configuration Compliance Process with Validation
By relying solely on manual methods, Enterprises will be incapable of ensuring the entire network remains in a state of compliance, so network teams must turn to a modern, automated approach to this challenge. The right automation approach should include the ability to support both CLI and API network devices and network services. This is critical because more and more modern network solutions and cloud-network services are configured and managed through APIs. In addition to supporting modern infrastructure, Enterprises that adopt an automated configuration compliance solution should also implement a validation process to ensure that any proposed configuration change is checked for compliance before it is actually applied to a live network device. This ensures that once the network is in a state of compliance, it stays there.
Itential provides an easy way for network teams to modernize their compliance checking process by building a network automation platform that was purpose built to support both CLI and API network devices at scale and overcome the challenge of ensuring the network is always operating according to the latest compliance standards. Itential’s Configuration Manager supports traditional reactive, scheduled configuration checking as well as modern, proactive configuration change validation to always ensure the network is operating at the highest level of security and reliability.
Legacy Tools
Itential Configuration Manager
Limited network support. Limited vendor support and lack of integration with API-based networks, which limits the ability to automate compliance and remediation across the entire network.

Support for all networks. Built-in CLI support for multiple network vendors, a process to define syntax for new network devices, and integration of APIs for modern and cloud networking. Automated compliance checks and validation for every network device and service.
Lack of proactive checks. Checks occur after a network change has been made and is running live, no concept of validating a change before it’s actually made.

Maintain maximum compliance. Validation ensures that any proposed change is checked for compliance before it is applied. If the change would make the device non-compliant, it’s not applied to the device.
Increased network risk. Lack of automated compliance checks and validation means there will always be areas of the network that are not compliant, even if it’s for a short window of time, and that means they are a risk to network security or network stability.

Optimal trust and confidence in the network. Automating compliance checks and validation means that every network device and service can be in a state of compliance, and any subsequent config changes will not put it out of compliance.
How to Automate Validation with the Itential Automation Platform
Itential’s configuration management capabilities empower the network team with an automated platform that can implement traditional compliance checking along with modern configuration validation so they can be sure that the entire network, not just a portion, is configured and operating properly. With native support for both CLI and API management methods, Itential is the only solution for modern enterprise networks that leverage both physical network devices and cloud-based network services, and can ensure consistent compliance, end-to-end across the entire network.
Get Started with Itential
Schedule a Custom Demo
Schedule time with our automation experts to explore how our platform can help simplify and accelerate your automation journey.
Take An Interactive Tour
See how Itential products work firsthand in our interactive tours.
Watch Demo Videos
Watch demos of Itential's suite of network automation and orchestration products.




