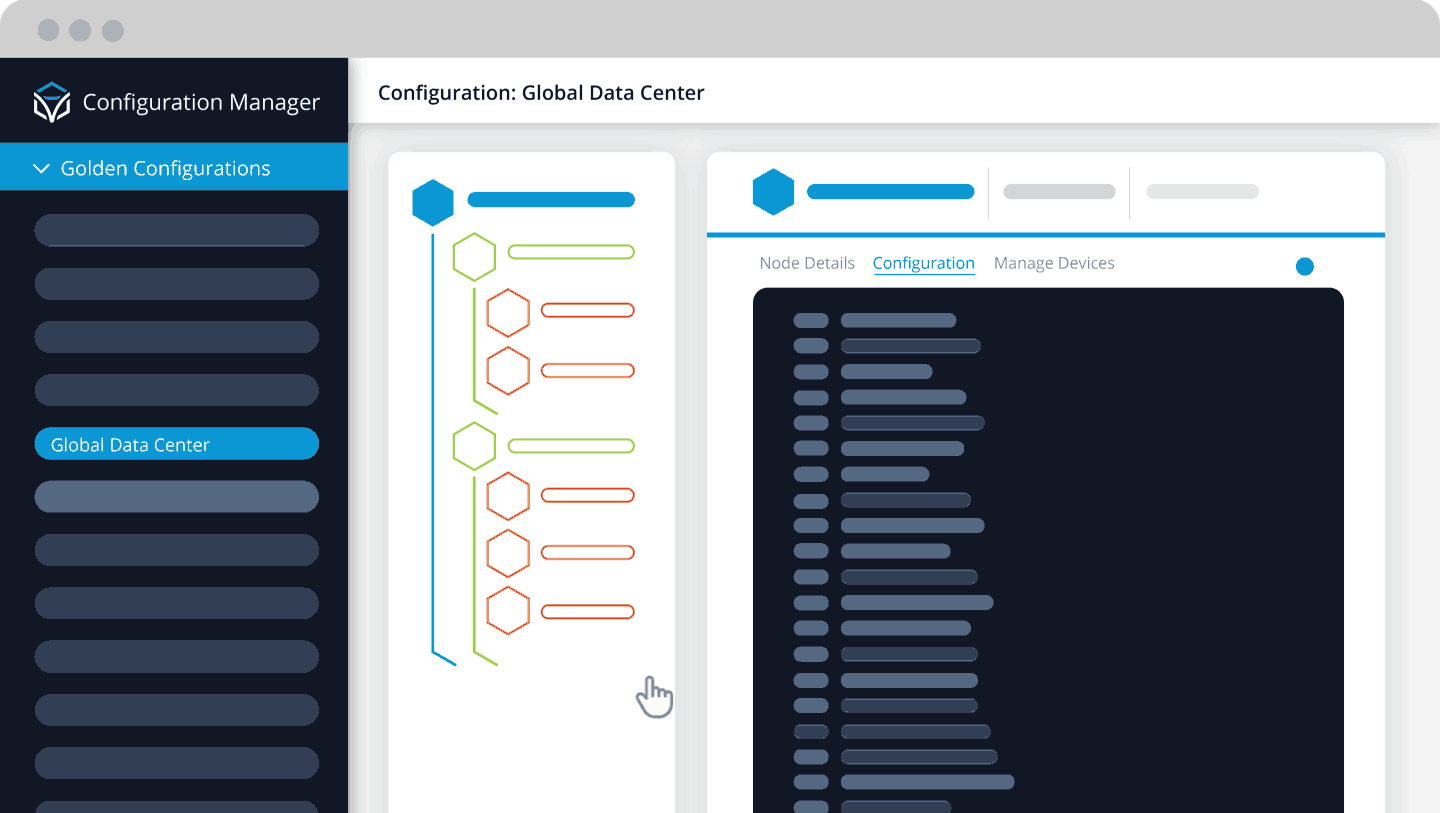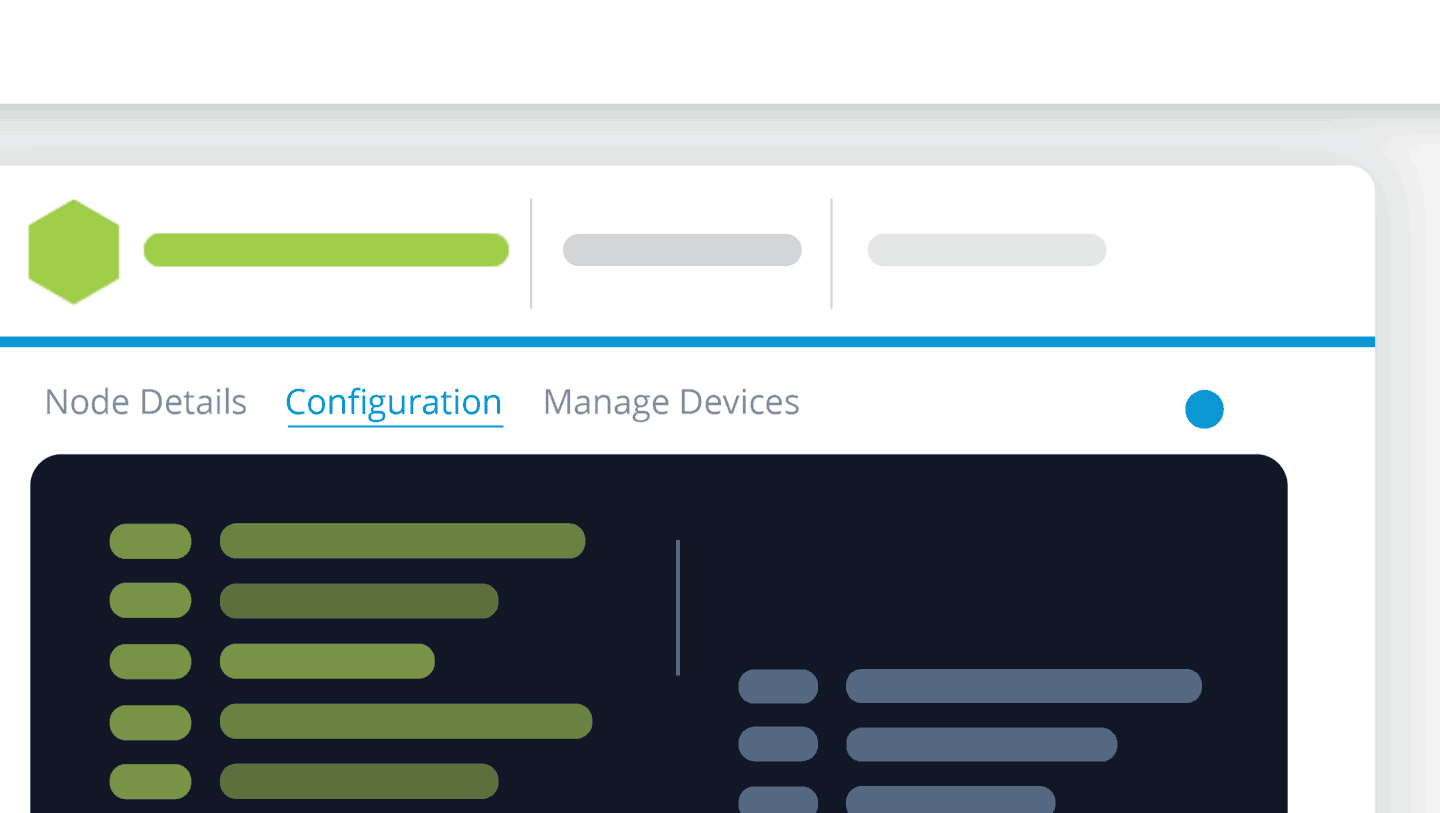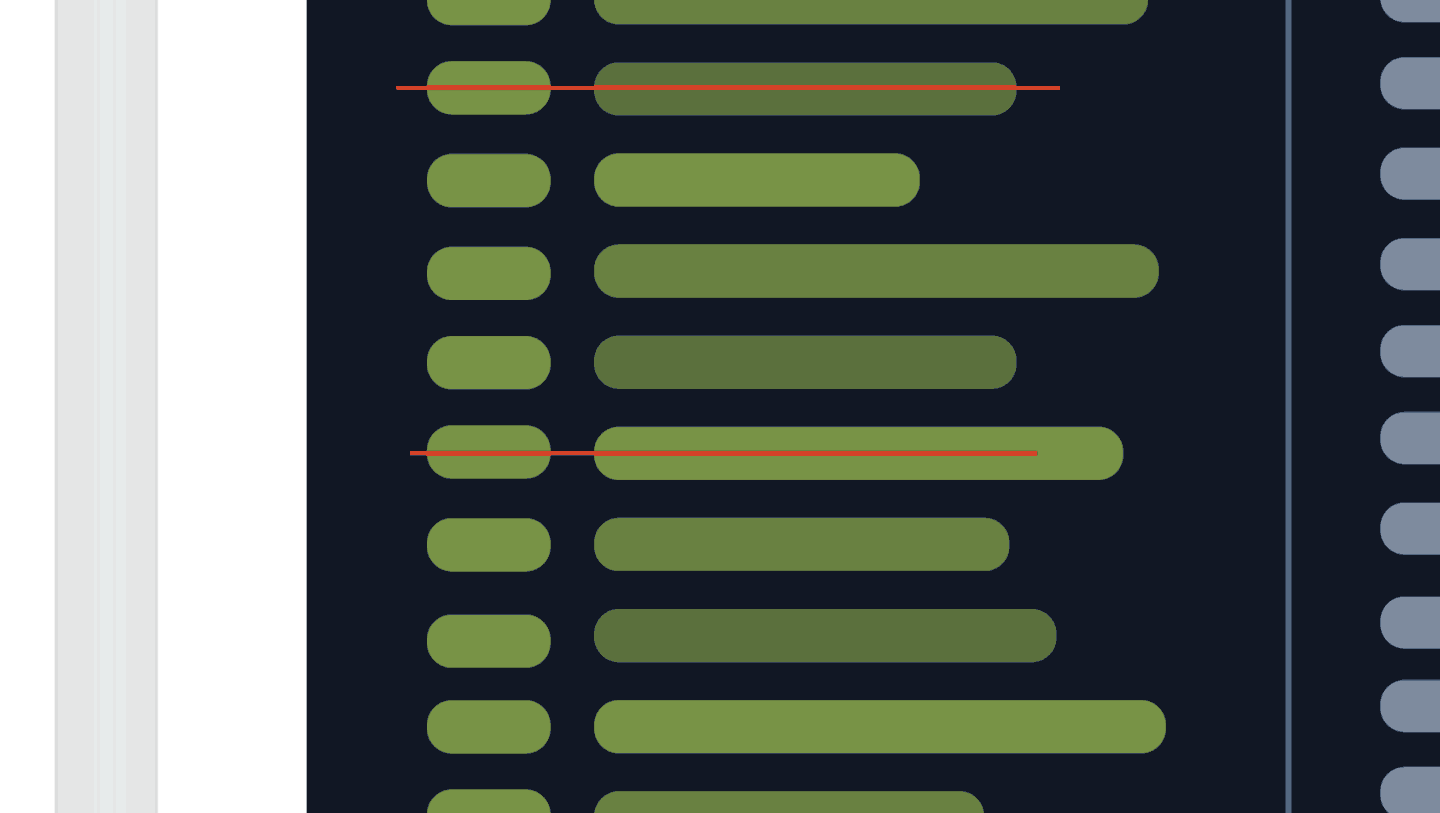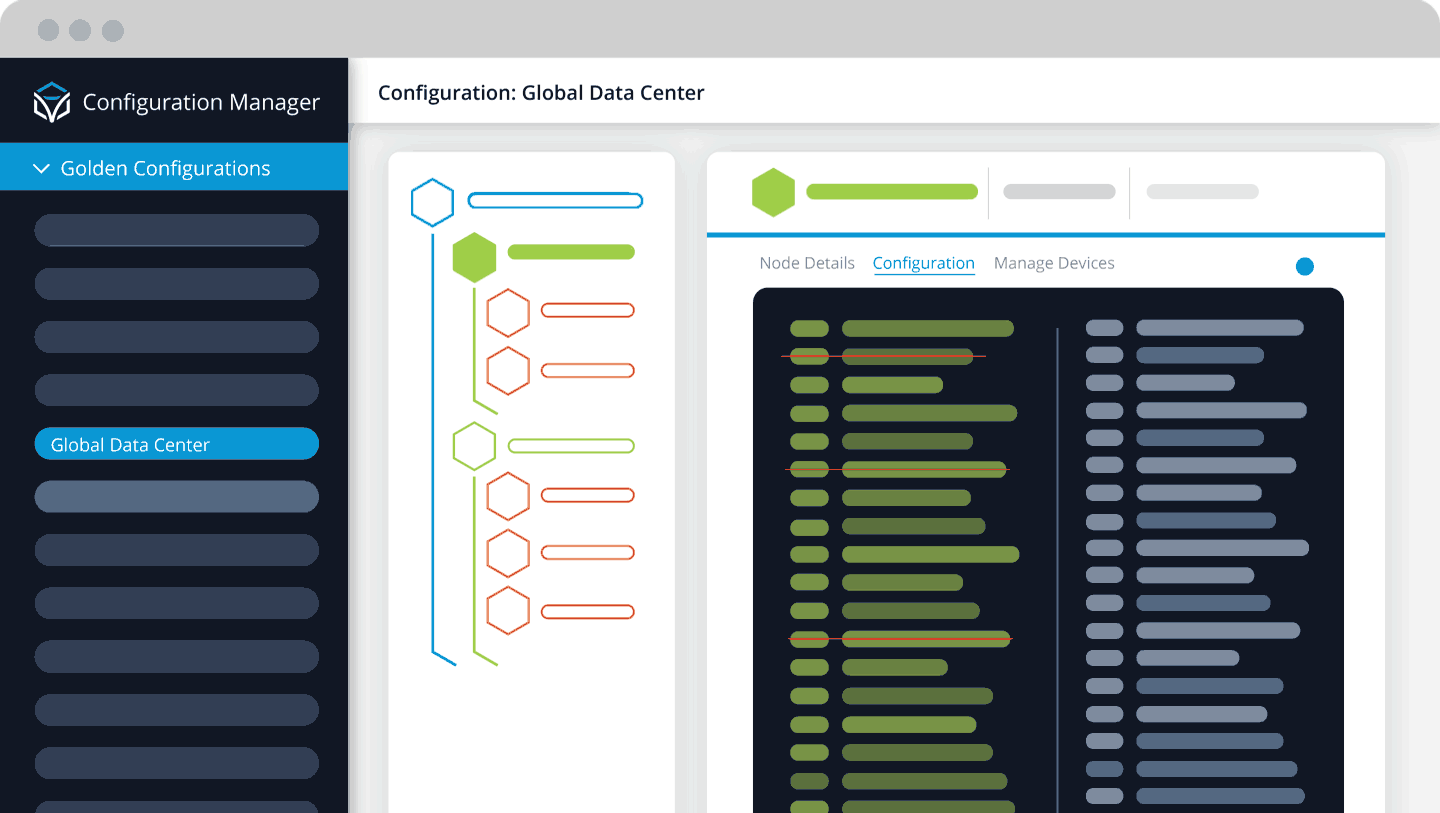
At the heart of configuration compliance is a standard, and that standard is a Golden Configuration. Without the ability to define a Golden Configuration file quickly and easily for a set of devices, network teams will struggle to bring the network into compliance and maintain compliance.
Network Configuration Management Creating Golden Configuration Templates
What is Golden Configuration?
A Golden Configuration for a network device is the standard by which the device should be configured. In effect, it becomes the set of rules that must be adhered to in the configuration of a particular device. If that device fails to meet the standard set by those rules, it is deemed to be “out of compliance,” and the device needs to be remediated, and its configuration is updated to bring it back into compliance with the Golden Configuration.
Is the Lack of Network Standardization Putting Your Business at Risk?
Network standardization is critical for the management of today’s complex network infrastructure. Every network must have a set of defined rules that determine how it should operate. These rules define the requirements to ensure security and access, reliability, and performance of the network, and may be driven from different sources like regulations, policies, or standardized best practices. To the end user, the network is consumed as a whole, but to the network team, the network is comprised of many individual devices and services and each of these elements must have a Golden configuration standard defined.
So ask yourself, are you still:
Defining Golden Configuration for critical network devices in your head?
It may be shocking, but many network teams do not have a tangible Golden Configuration standard defined anywhere, even for their most critical network devices. Based on experience, some team members have an instinctive knowledge of how a device should be configured, but configuration requirements and standards will change over time and should not be left only to one’s memory.
Storing Golden Configuration in a file?
Golden Configurations defined in text files are static and inflexible. Network teams must have modern tools that allow them to collaborate to define sections of configuration standards, and allow rules to allow, disallow, or ignore lines of configuration. Also, support for well-known technologies like regular expression and templates help create very flexible and dynamic golden configurations that can apply to groups of devices.
If yes to either of these, it’s undoubtedly time to automate.
A modern solution to help network teams in defining Golden Configurations, applying them to devices to determine compliance, and remediating any changes are the foundation for any enterprise that is serious about ensuring they have the most secure, resilient, and high- performance network possible.
Why It’s Time to Modernize Your Golden Configuration
The network team is responsible for running the most secure and reliable network possible, and they cannot accomplish that lofty goal by attacking a modern problem with legacy tools. Instead, enterprises should invest in a modern solution for their network teams that enable them to collaborate together to create and maintain Golden Configuration standards across the entire network, whether physical, virtual, or cloud. Without a modern solution that can automate Golden Configurations, compliance, and remediation the network will continue to exist in a state of unneeded and unnecessary risk.
Itential provides a complete platform for network teams to work together to build dynamic and flexible Golden configuration templates in a single, central application.
Legacy Tools
Itential Configuration Manager
Limited, static configuration template. Using text files to store a standard configuration template is static, inflexible and will limit the ability to ensure the network is operating correctly.

Robust flexible Golden Configuration tree. A dedicated application that supports teams collaborating, using a tree structure to segment applicable configurations. Configurations are reusable and support dynamic elements like variables, regular expressions, and Jinja2 templates.
Gaps in support for CLI devices. Relying on a solution provider to write code to support a new CLI type is a problem. If a device isn’t supported, you can’t define a standard, and check for compliance. This leaves large portions of the network exposed and vulnerable.

Support for any CLI syntax from any vendor. Itential supports all of the top network vendor’s CLIs by default. We understand that supporting any device’s CLI is critical so a customer can quickly define a CLI syntax themselves and integrate the new device into the application, ensuring that Golden Configurations can be created for these devices and checked for compliance.
No compliance for API-based networking. Compliance is required across the entire network, and that includes network solutions that use API methods of management instead of CLI. Without proper API support, a Golden Configuration cannot be built for these types of network elements.

Complete API integration for modern networking. Build your Golden Configurations for CLI and API based network devices and services in a single application, allowing network teams to treat API-based networking services like they were traditional network devices.
Unable to effectively manage secure access to tools. Multiple tools for multiple users leads to chaos in the network. Managers need insight on what tools are available to which users, and accountability when they are used.

Complete RBAC control. Secure access to a platform that provides the right people with the right tools with access to the right devices or services in the network. Integration with AAA systems, and logging for every action executed.
A Modern Approach to Golden Configuration with the Itential Automation Platform
Itential’s configuration management capabilities not only enable teams to build Golden Configurations, but it also provides the ability to assign groups of devices to the Golden Configuration tree and generate a compliance report for every device in a single click. If any devices are out of compliance, automated intelligent remediation of the device is available when the network team is ready to make changes.