Get a headstart on preparing your lab for an Itential Proof of Concept.
What to Expect During Your PoC
Your Proof of Concept (PoC) will allow you to evaluate the Itential Automation Platform (IAP) and Automation Gateway (IAG). During the PoC, you will be hands-on with Itential’s software, building automations in a low-code environment with guidance from the Itential team. Upon completion of the PoC, we will present the automations and use cases that we’ve created over the course of the week to a wider audience within your organization.
Before your PoC can start, you will need to prepare a lab server meeting the requirements below to host both IAP and IAG in your environment. The Itential team will work with you to install software.
Server Requirements
Customer will provide a dedicated server on which Itential Automation Platform and Itential Automation Gateway will be deployed as Docker containers.
Resource Requirements
- Can be deployed on physical hardware or as a virtual machine
- 64-bit Red Hat Enterprise Linux or Rocky 8+
- 8 64-bit CPU Cores
- 16 Gigabytes of RAM
- 200 GB of Storage
- At least 50 GB free in
/opt- To be used for the installation file download and extraction
- At least 50 GB free in
/var/lib- To be use for docker containers and processes
- At least 50 GB free in
- root/sudo access for docker commands (docker load, docker compose up/down)
Software Requirements
- Docker (Latest Stable)
- Docker Compose (Latest Stable)
Network Requirements
- Internal Access to Itential Automation Gateway (8083/tcp)
- Internal Access to Itential Automation Platform (3000/tcp, 3443/tcp)
- IP Connectivity
- Device and System Integrations
- Trial License Validation (https://api.keygen.sh)
- DNF RPM Repositories
- Python PIP Repositories
- Client VPN Access for Itential Engineers
Proxy Configuration via Docker
- https://docs.docker.com/network/proxy/
Itential Connectivity
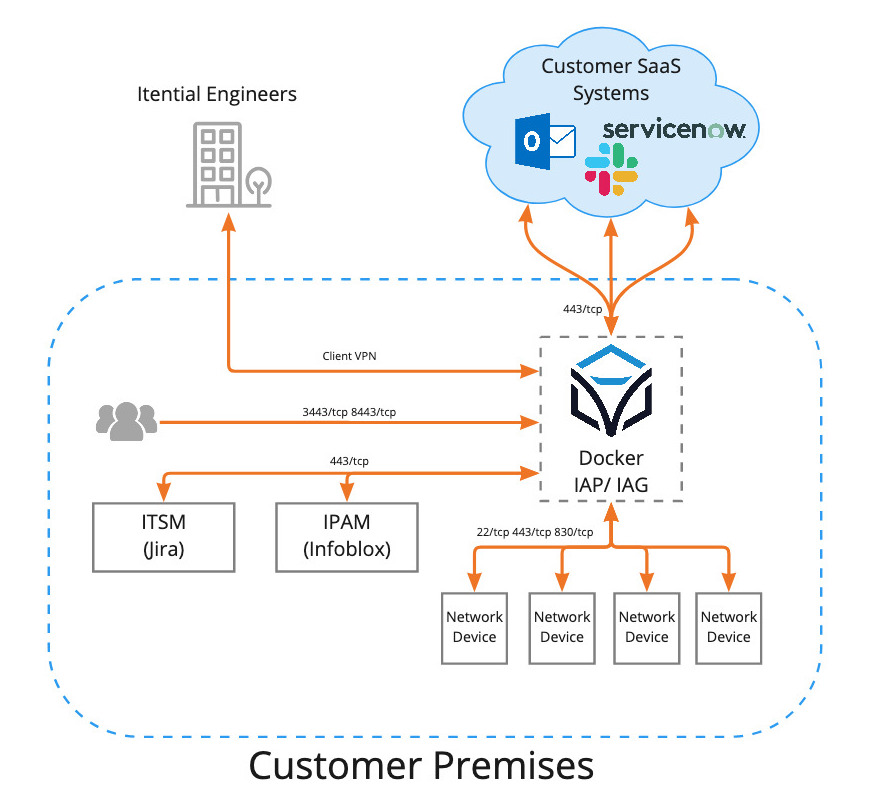
IAP/IAG Connectivity Testing
SSH Device Connectivity
For each network device to be managed via SSH, test connectivity using the command below.
Command
ssh <user>@<hostname>Example
> ssh admin@csr1000v-1
(admin@csr1000v-1) Password:
csr1000v-1#
Rest Device Connectivity
For each network device to be managed via REST, test connectivity using the command below.
Command
curl https://<hostname>:<api_port>/<api_endpoint>
Example
> curl https://192.168.0.100:8443/api
{"result": "success"}
>
NETCONF Device Connectivity
For each network device to be managed via NETCONF, test connectivity using the command below.
Command
ssh <user>@<hostname> -p 830 -s netconf
Example
> ssh admin@csr1000v-1 -p 830 -s netconf
(admin@csr1000v-1) Password:
<?xml version="1.0" encoding="UTF-8"?>
<hello xmlns="urn:ietf:params:xml:ns:netconf:base:1.0">
<capabilities>
<capability>urn:ietf:params:netconf:base:1.0</capability>
_truncated_
</capabilities>
<session-id>21</session-id></hello>]]>]]>
Integration Connectivity
For each system integration, test connectivity using the command below.
Command
curl https://<hostname>:<api_port>/<api_endpoint>
Example
> curl https://192.168.0.100:8443/api
{"result": "success"}
>