The Need for Automating Configuration & Compliance
When it comes to network automation, most teams believe they must get their network in order before they even consider implementing automation. While this may have worked in the past when the network was mainly physical devices that grew at a manageable pace, it is not sustainable in today’s modern and distributed IT environment. The network is no longer composed of only physical routers and switches in a data center. It is growing more rapidly than ever, and much of it is centered around deployments in the cloud, whether cloud-native network services like VPCs or transit gateways or cloud-based network and security services.
Current network configuration management tools do not provide the support needed to manage this new landscape in an efficient and effective manner.

Almost 70% of network management professionals are NOT satisfied with the tools and processes they use for network configuration management according to research from Enterprise Management Associates and Itential. The lack of tools makes it very hard for network teams to keep up with the changes required in today’s hybrid landscape.
This poses a big challenge for network teams – how do you keep your ENTIRE network in compliance by adhering to your chosen set of configuration standards? The answer lies in automation.
Defining Network Compliance
The word “compliance” can mean a lot of things depending on your industry or job function. So, let’s start by defining what compliance means in the network. Network compliance is the adherence to the network standards set by your organization. These standards fall into at least one, but probably several, of the following categories:
In the drive to the cloud, not all organizations are in a position to rip-and-replace what they’ve already built. There are many forms of traditional compute, storage, and networking resources that will need to be integrated into any cloud compute or networking plan.
Networking must adapt to this hybrid and multi-cloud reality while retaining the capability to connect to traditional infrastructure, including routers, switches, and firewalls, which despite cloud remain the lifeblood of connectivity for enterprise IT assets. Networking infrastructure has developed over several decades as waves of computing paradigms have transformed IT organizations. Over the course of time, it has become more challenging to manage this diverse environment spanning legacy enterprise to cloud native.
The networking infrastructure might include a wide variety of technologies and approaches: software-defined networking (SDN) for private or cloud resources; traditional underlay networks, including routers and switches; software-defined wide-area networking (SD-WAN) for enterprise branches; or application-layer cloud networking approaches such as service mesh.
Security

Perhaps the most important parts of network standards defined by an organization are the configurations that keep network devices and services secure. Security standards should be uniformly applied across every area of your network because one single insecure element can bring a network down or lead to a data breach.
Reliability

Organizations never want their network to go down. In fact, most can’t afford for it to go down. Correct configurations ensure networks stay reliable with proper failover and redundancy features to keep end users connected at all times.
Performance

The performance of a network is contingent on proper configuration. If applications are running slowly, the network is the first to be blamed. That’s why configurations must be consistent and up-to-date to ensure the network is operating at peak performance.
Drivers of Network Compliance
The network standards defined by an organization are driven by a handful of both internal and external factors.
External Regulations
Regulatory items such has HIPAA, PCI, etc. centered around data security, privacy, and other aspects of the business.
Run the Business Needs
Businesses need to deliver more services faster to internal and external customers, which requires reliable networks.
Business Strategy
As businesses need applications to scale up, the network needs to scale up as well, so it doesn’t impede business growth or time-to-market.
Redefining Network Compliance in a Hybrid-Cloud World
Most thought moving applications and infrastructure to the cloud would simplify things, particularly networking, but it has added significant complexity to most networks. The introduction of cloud computing has made the enforcement of compliance standards increasingly complicated. Typical organizational structures where network and cloud teams are working in silos have only exacerbated the problem. In fact, 73% of enterprises have experienced security and compliance issues because of poor collaboration between the two groups.
Every single network component and cloud platform has a configuration of some sort that must be enforced. The hard truth is that each component and platform is not accessed or managed the same way, but they all have a configuration that must be applied in order to meet an organization’s standards. This hybrid-cloud world requires a new, modern solution to drive configuration compliance and manage it in a unified manner.
The 3 Components to a Modern Network Compliance Solution
When it comes to modern network compliance, there are three things that must be adopted to achieve compliance in a hybrid-cloud world:

01
The ability to create and enforce a Golden Configuration across CLI network devices, cloud network elements and controller/application APIs.

02
The ability to automate the remediation of compliance issues
03
The ability to validate changes to devices before they are made.
01 Create & Enforce a Golden Configuration Standards Across CLI & API
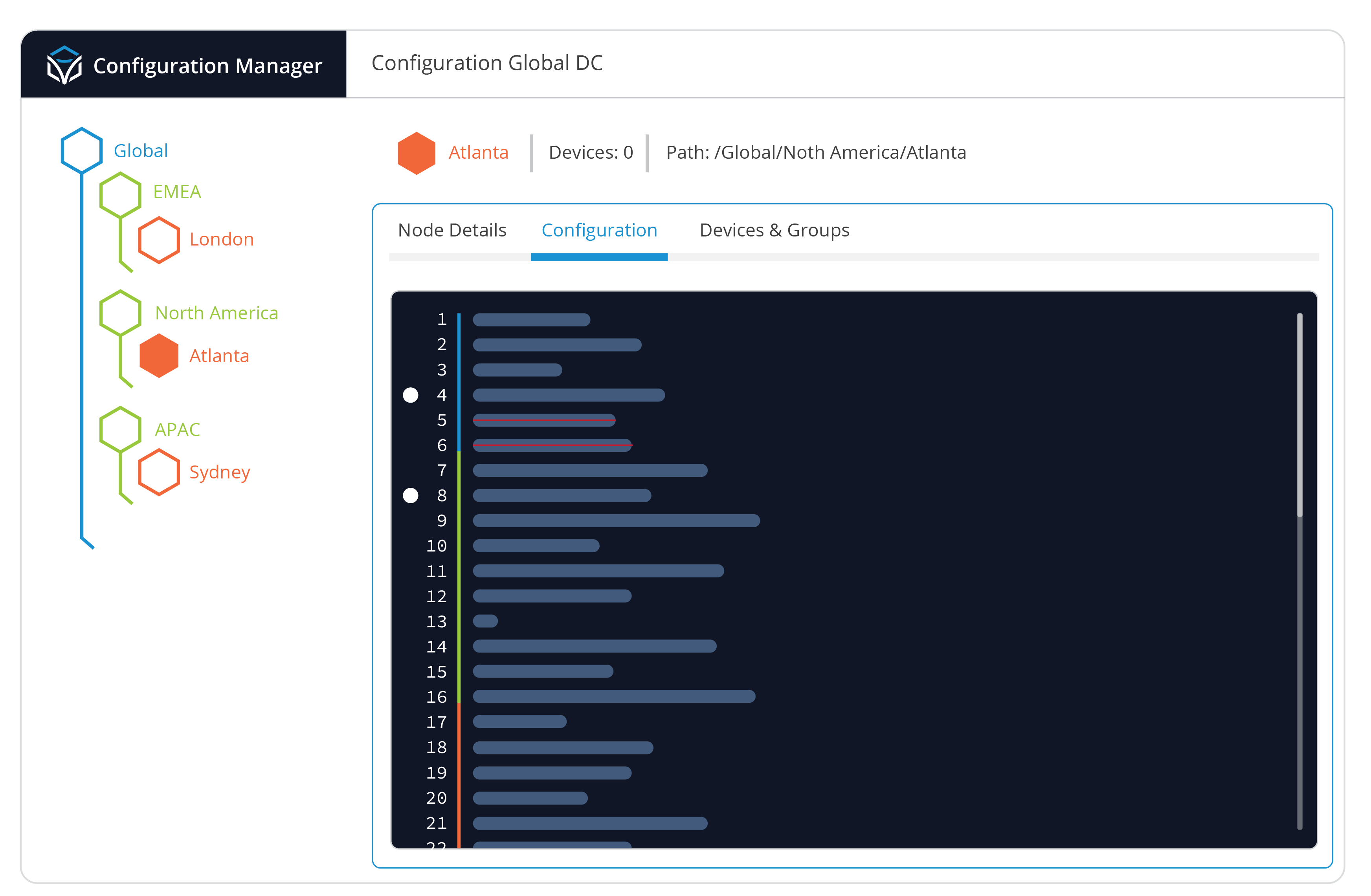
The network standards set by an organization can be captured in Golden Configurations. The only way to ensure your network adheres to its standards is by creating and enforcing Golden Configurations across CLI network devices, cloud network elements, and controller/application APIs.
Building flexible and modular Golden Configurations that can be applied to multiple device types across multiple domains is often difficult or impossible with traditional NCCM tools. Many network teams end up with nearly as many Golden Configuration files as they have network devices, which defeats the purpose of a Golden Configuration. Traditional solutions also typically do not include a way to support network solutions that use APIs, like cloud networking.
Modern solutions must be adopted that allow an organization to apply their network standards to any device in any domain, or they will never fully comply with those standards.

- Create dynamic and flexible Golden Configuration templates for any device and any service across network and cloud infrastructure.
- Reduce the number and complexity of your Golden Configurations so nothing in the network is overlooked and the network always adheres to the desired standard.
- Easily add, modify, and remove configuration lines and the changes will be inherited to child nodes based on location in the Golden Configuration tree.
02 Automated Remediation of Configurations that have Drifted out of Compliance
What happens when a device drifts out of its defined Golden Configuration, meaning it becomes out of compliance? Organizations must be able to quickly and easily remediate whatever this issue is. The first step to remediation is understanding which devices and services are outside of compliance. Network teams must then correct the configurations of these network devices and services for them to become compliant again.
One major component traditional NCCM tools lack is the ability to automate the remediation of any device that drifts out of compliance.
Given the high number of network devices and services that would need to be manually configured, it’s important to understand that a flexible process of automating these changes is necessary. In some cases, with certain configuration changes, it may be acceptable for an automation to automatically remediate. In other cases, certain changes may require human oversight, or the need to make changes during a maintenance window. The key is to enable network teams the ability to create the automations with the appropriate logic to address remediation efficiently. Otherwise, it will only create another backlog of work for the team.

- Automate the remediation of both physical devices and cloud services that are out of compliance.
- Proactively schedule compliance checks and ensure your entire network is in compliance before it experiences security or reliability problems and detect non-compliant assets rapidly.
- Provide historical reports of device compliance, help identify and eliminate persistent issues.
03 Validate Configuration Changes Before They Are Applied to the Network
One of the most valuable components of modern network configuration is the ability to validate a proposed change for compliance before it’s even made. This can easily mitigate a potential error before it’s applied.
Many network teams are still managing their configuration process in a very reactive way, causing high concern that most changes have the possibility to bring their networks out of compliance. This traditional, reactive method of ensuring a network configuration is in compliance can be summed up as a “break, check, fix” process – a change to the network is detected that has broken the standard (the break), the change is detected (the check), and a network engineer must manually correct the configuration to bring it back into compliance (the fix).

Relying on this methodology alone in today’s security-driven environment results in greater exposure to security risks and potential network outages. Instead of working solely on reactive processes, organizations need to implement proactive measures that can prevent the “break” event from occurring in the first place by employing a more proactive approach to network changes and configuration management.

Network teams can help ensure the network stays in compliance by using validation techniques, which provide feedback on a proposed change to a device, to determine whether the proposed change violates any Golden Configuration policy before it’s applied. Because changes have not actually been applied to a network device or service, this takes a proactive approach to compliance. By shifting from today’s reactive method that traditional solutions take, teams that take a modern approach of implementing validation into the process of network changes can ensure their network stay in compliance.

- Validate a change before it’s made, eliminating exposure due to configuration drift.
- Quickly create and publish self-service automations, that include validating changes before they are made to ensure compliance when automating.
- Unify your change processes with automation for a fully integrated approach to configuration management.
You Will Never Have a Compliant Network without Automation
One key element to each component of a modern network compliance solution is automation. Each of these components is centered around the idea that both compliance and automation are coupled together, rather than managed in siloes. Here’s why:
Compliance without Automation Creates More Manual Backlog
The rapid growth of the network from on-prem into the cloud has led to an increased network complexity that existing compliance tools simply cannot address as they are limited in scope, scale, and features. They can’t keep up with the pace of supporting all the different vendors that teams were deploying in the on-prem network, and they had severe limitations regarding automation. These tools can generate compliance reports, but still required a human to remediate the devices. Network teams dealt with all these limitations, and used them to the best of their abilities, but that still meant that only parts of the network were compliant, and ultimately created more manual backlog as the network has grown in size and complexity.
Automation Without Compliance Creates Additional Bad Network Configurations
Making network changes manually has become a bottleneck in the plan to deploy IT infrastructure rapidly. If network teams are expected to deploy and change the network more rapidly than ever before, they must adopt new automation techniques to see success. This automation solution has to address the entire network infrastructure, on-prem and cloud. But, if your focus is only on automating infrastructure quickly without compliance oversight, this can also lead to an even greater proportion of the network that is not in compliance.
Automation alone may solve the problem of reducing manual processes to deploy network changes quickly, but it can also lead to more compliance issues in the newly deployed infrastructure.
It is critical that compliance and automation work together to achieve the goal of quickly deploying a network that always adheres to the compliance standards.
How Itential is Redefining Modern Configuration Management
Network and IT teams deserve better solutions than what has been provided to date. The days of manual configuration changes and disaggregated solutions are over.
The Itential Automation Platform is breaking the cycle and providing network teams with a modern platform that couples compliance and automation together so they no longer have to be managed in disparate applications with pockets of automation. By taking a collaborative approach, teams can achieve the goal of quickly deploying any network infrastructure, whether on-prem or cloud, that’s compliant from the first day to the last.
Itential Configuration Management Capabilities
The only product built for modern network & cloud configuration & compliance automation.
The Itential Automation Platform was purpose-built to help organizations ensure their networks are always in compliance, with the capabilities tailored to support each of these components that matter most. With Itential, network teams can:
- Quickly create Golden Configuration templates for both CLI network devices and cloud-based services that use APIs for management.
- Easily integrate with any network, on-prem, controller or cloud to quickly build automations without writing a single line of code.
- Run compliance reports for any devices and services on the network in a single interface, and automatically remediate the configuration of any device that is not compliant.
- Validate proposed configuration changes to the network to ensure, before they are even applied, that the changes will not break the compliance standard.