Overview
A Developer Architecture (DA) is an Itential architecture where all of the components are installed as singletons and can not gracefully tolerate failures. This architecture is not recommended for production environments and testing environments that require strict uptimes and redundancies. This architecture is suitable for development environments only. The IAP application performs many reads and writes against the database and is sensitive to great latencies. All components must be installed in the same datacenter. All components must have authentication enabled.
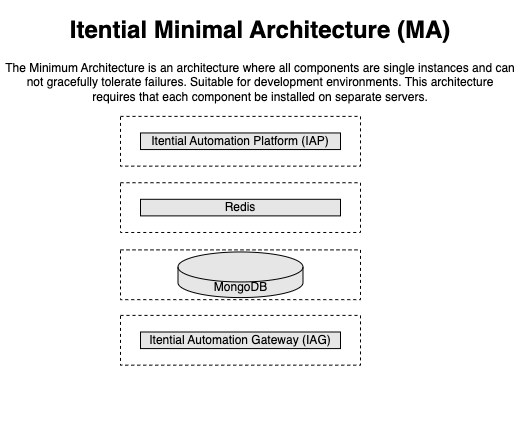
The DA architecture is comprised of 4 VMs broken down as follows:
- 1 IAP server
- 1 MongoDB server
- 1 Redis server
- 1 IAG server
Server Specs
Itential Enterprise Server
| CPU | 64-bit x86 CPU cores | 8 |
| OS | RHEL Rocky |
8, 9 8, 9 |
| RAM | DDR5 DRAM 3200 Mhz | 32 GB |
| Disk (Solid State media,ie. SSD, NVMe) |
Total /var/log/itential /opt/itential |
250 GB 100 GB 100 GB |
MongoDB Server
| CPU | 64-bit x86 CPU cores | 8 |
| OS | RHEL Rocky |
8, 9 8, 9 |
| RAM | DDR5 DRAM 3200 Mhz | 64 GB |
| Disk (Solid State media,ie. SSD, NVMe) |
Total /var/log/mongo /data |
1000 GB 150 GB 850 GB |
Redis Server
| CPU | 64-bit x86 CPU cores | 4 |
| OS | RHEL Rocky |
8, 9 8, 9 |
| RAM | DDR5 DRAM 3200 Mhz | 16 GB |
| Disk (Solid State media,ie. SSD, NVMe) |
Total /var/log/redis |
100 GB 100 GB |
IAG Server
| CPU | 64-bit x86 CPU cores | 8 |
| OS | RHEL Rocky |
8, 9 8, 9 |
| RAM | DDR5 DRAM 3200 Mhz | 16 GB |
| Disk (Solid State media,ie. SSD, NVMe) |
Total | 50 GB |
Hardware & Hypervisor Configurations
Processor
The processor specification requirement is as follow:
- Second generation or better Intel Xeon Platinum 8000 series processors.
- Third generation or better AMD EPYC 7000 series processors.
Memory
The memory specification requirement is as follow:
- DDR5 DRAM 3200 Mhz or higher
Storage
The storage performance requirement in IOPS (16 kiB) is as follows:
- 20000+ IOPS
- Non-spinning media (i.e. SSD, NVMe)
Network
The network speed requirement is:
- 10 Gbps or higher
Note: In some instances, adding additional dedicated interfaces that are focused on routing specific traffic to specific external systems can be explored further. This routing of traffic would be configured at the OS-level (custom interfaces and routes) and require the system administrator to manage this. An example would be separating NSO traffic from Redis/Mongo destined traffic.
Hypervisor/Host OS Settings
These settings are strongly recommended for high load applications of IAP:
- CPU affinity settings or similar functionality to prevent CPU starvation
- Full Memory Reservation
- One physical CPU per VM is preferred
- Huge pages for memory support enabled
- Except MongoDB
Note: MongoDB discourages the utilization of Transparent Huge Pages
- Except MongoDB
- Memory compression disabled
- Minimal CPU Allocation settings for scheduler according to CPU clock
- Example: assuming an IAP VM on a server capable of 2.5GHz nominal speed: CPU clock reservation = 16vCPU * x 2.5GHz
Note: Please follow Hypervisor recommendations when performing CPU reservations. In most cases the total of all CPU reservations for all VMs on a host cannot be more than 90% of the host capacity as 10% is reserved by the host itself.
Ports & Networking
In an environment where components are installed on more than one host, the following network traffic flows need to be allowed. All is TCP protocol unless otherwise noted. Not all ports will need to be open for every supported architecture. Secure ports are only required when explicitly configured.
| Souce | Destination | Port | Description |
|---|---|---|---|
| Desktop Devices | IAP | 3000 | Web browser connections to IAP over HTTP |
| Desktop Devices | IAP | 3443 | Web browser connections to IAP over HTTPS |
| Desktop Devices | IAG | 8083 | Web browser connections to IAP over HTTPS |
| Desktop Devices | IAG | 8443 | Web browser connections to IAP over HTTPS |
| Desktop Devices | Hashicorp Vault | 8200 | Web browser connections to Hashicorp Vault |
| IAP | MongoDB | 27017 | IAP connects to MongoDB |
| IAP | Redis | 6379 | IAP connects to Redis |
| IAP | Redis | 26379 | IAP connects to Redis Sentinel. Required only for HA installations. |
| IAP | IAG | 8083 | IAP connects to IAG over HTTP. |
| IAP | IAG | 8443 | IAP connects to IAG over HTTPS |
| IAP | Hashicorp Vault | 8200 | IAP connections to Hashicorp Vault |
| IAP | LDAP | 389 | IAP connections to LDAP When LDAP adapter is used for authentication |
| IAP | LDAP | 636 | IAP connections to LDAP with TLS When LDAP adapter is used for authentication |
| IAP | RADIUS | 1812 | IAP connections to RADIUS When RADIUS adapter is used for authentication. This uses UDP. |
| MongoDB | MongoDB | 27017 | Each MongoDB talks to the other MongoDBs for replication of the database. Required only for HA installations. |
| Redis | Redis | 6379 | Each Redis talks to the other Redis’s for replication. Required only for HA installations. |
| Redis | Redis | 26379 | Each Redis uses Redis Sentinel to monitor the Redis processes for HA resiliency. Required only for HA installations. |
Required User Accounts in Dependencies
The validated designs are very opinionated installations of Itential and its dependencies. The following user accounts are required by the dependencies for a validated design and are used for the following purposes.
MongoDB
| Account | Description |
|---|---|
| admin | Has full root access to the mongo database. Can read and write to any logical database. Can be used to issue admin commands like forcing an election and configuring replica sets. This is NOT used by the Itential application but is created for admin purposes. |
| itential | Has read and write access to the “itential” database only. This is the account used by the IAP application. |
| localaaa | Has read and write access to the “LocalAAA” database. This is used by the Local AAA adapter for local, non-LDAP logins. |
Redis
| Account | Description |
|---|---|
| admin | Has full root access to the Redis database, all channels, all keys, all commands. This is NOT used by the Itential application but is created for admin purposes. |
| itential | Has full access to the Redis database, all channels, all keys, EXCEPT the following commands: asking, cluster, readonly, readwrite, bgrewriteaof, bgsave, failover, flushall, flushdb, psync, replconf, replicaof, save, shutdown, sync. This is the account used by the IAP application. |